说在前面的话
1、在kali中metasploit默认使用postgresql作为它的数据库;
想要开启metasploit服务首先得打开postgresql数据库, 命令如下:(或者:/etc/init.d/postgresql start); 因为在kali中所有的服务都不是默认开机自启的, 所以想要开机自启,命令如下:update-rc.d postgresql enable。2、初次使用数据库服务时需初始化,以便创建系统默认的数据库及数据库用户; 命令如下:msfdb init(默认创建的数据库名:msf,msf_test;用户名:msf;口令默认为空)
3、接下来就是启动metasploit的时候了;
在kali2.0之后,只需启动msf控制台即可; 命令如下:msfconsole。 (kali2.0之前的命令是这样的:service metasploit start;对于2.0之后不管用)
问题详情
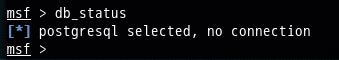
msf > db_status[*] postgresql selected, no connectionmsf >

运行 service Metasploit start 无任何反应,提醒报错:Failed to start metasploit.service: Unit metasploit.service failed to load: No such file or directory.
解决办法
对于命令解释
msfdb init # initialize the database msfdb reinit # delete and reinitialize the database msfdb delete # delete database and stop using it msfdb start # start the database msfdb stop # stop the database
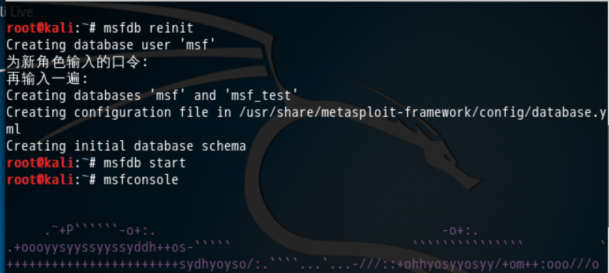
root@kali:~# msfdb reinitCreating database user 'msf'为新角色输入的口令: 再输入一遍: Creating databases 'msf' and 'msf_test'Creating configuration file in /usr/share/metasploit-framework/config/database.ymlCreating initial database schemaroot@kali:~# msfdb startroot@kali:~# msfconsole .~+P``````-o+:. -o+:..+oooyysyyssyyssyddh++os-````` ``````````````` `+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o++++///~~~~///++++++++++++++++ooyysoyysosso+++++++++++++++++++///oossosy--.` .-.-...-////+++++++++++++++////~~//++++++++++++/// `...............` `...-/////...` .::::::::::-. .::::::- .hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo :Nm-/NMMMMMMMMMMMMM$$NMMMMm&&MMMMMMMMMMMMMMy .sm/`-yMMMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMMh` -Nd` :MMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMh` -Nh` .yMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMm/ `oo/``-hd: `` .sNd :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMm/ .yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMd .shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o+++oooo++/ `///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os: /MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+ -hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`:: .sMMmo. -dMd--:mN/` ||--X--|| ||--X--||........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........=====================================================================================================+--------------------------------+==============================================| Session one died of dysentery. |==============================================+--------------------------------+========================================================================================================= Press ENTER to size up the situation%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April 25, 1848 %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: 12975 mg %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Press SPACE BAR to continueValidate lots of vulnerabilities to demonstrate exposurewith Metasploit Pro -- Learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ]+ -- --=[ 1597 exploits - 912 auxiliary - 274 post ]+ -- --=[ 458 payloads - 39 encoders - 8 nops ]+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]msf > db_status[*] postgresql connected to msfmsf >
则,可以成功!